Wireless Design for the Big Return to Office

Wireless Design for the Big Return to Office
A Checklist for Building or Refreshing Your Wireless Office Network By Keith Heckel Jr., Pre-Sales Solutions Engineer at Aspire Technology Partners As more organizations return to their offices, they find that older networks – especially wireless networks – may not be up to the task. We have seen a wide spectrum of cases, from “Greenfield” […]

Implementation and General Overview of VLAN Trunking Protocol (VTP)
By Michael Keller. Senior Consulting Engineer at Aspire Technology Partners Introduction VLANs are a core component of networking and are critical in their utility spanning across a plethora of architectures, including Data Center, Wireless, UC and just about every base switching architecture there is. Their importance in networking goes without saying. They are still the […]
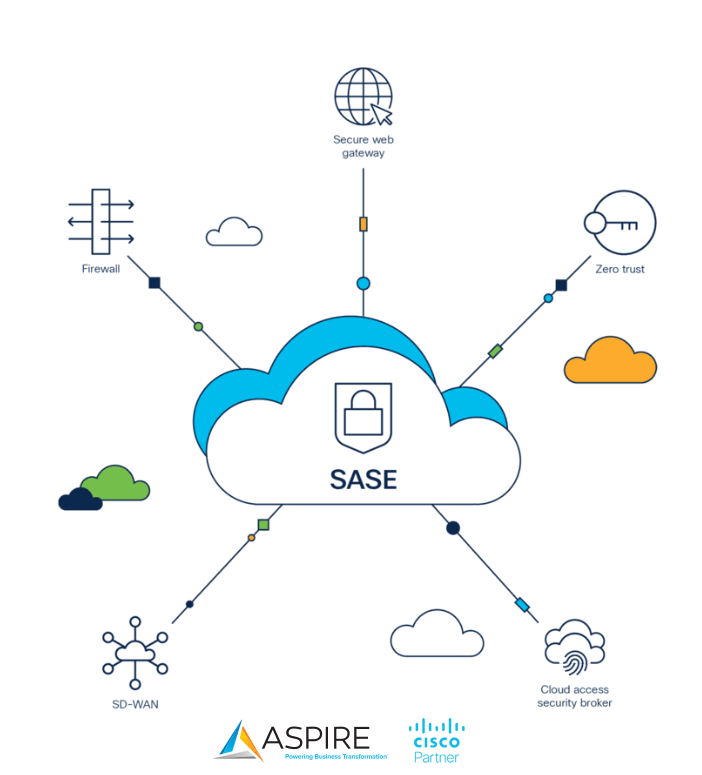
What is SASE, and why is it important?
By Manuel DeGuzman, Enterprise Network Solutions Architect The Changing Network Landscape The way we work has evolved, reshaping our networking and security landscapes. Mass adoption of Cloud applications and Software as a service (SaaS) in our everyday lives adds to the complexity of managing and securing our networks. Over a third of enterprise workloads are […]

Wireless Network Surveys
How Wireless Network Surveys Help You Increase Performance, Reduce Latency, Improve User Experience By Keith Heckel Jr., Pre-Sales Solutions Engineer at Aspire Technology Partners Following the “Enterprise Exodus” of the pandemic, employees, customers and other on-site visitors are encouraged to return to what may not always be a familiar place. Refreshed workplaces accommodate a new […]

Safety & Security in Schools: Looking Beyond Closed Doors
Safety and security in schools are constantly evolving. By Aspire Technology Partners Security Practice Experts Parents and the community demand safe schools, whether it’s a single building, a multiple-building campus, or multiple campuses across the region. Recent events only reinforce the need to secure, monitor, and protect students, faculty, and staff. Protecting people and property […]

Navigating a Hybrid, Modernized Work World
A Four-Part Checklist for Hybrid Work Success By Joe Latessa, Senior Account Manager at Aspire Technology Partners For much of the business world, the term hybrid has come to mean more than a car that runs on gas and EV. Instead, it has come to represent the way that the business now works. Employees who […]

How do you steal 1 million Facebook account credentials?
A large-scale phishing scam used Facebook Messenger to potentially impact millions of Facebook users. by Aspire Technology Partners Cybersecurity Team We see unusual emails in our inboxes daily. Many are easily identified when we see poor grammar or incorrect spelling. Yet phishing attacks are still successful, providing access to secure accounts every day. In some […]

Solving the Cybersecurity Conundrum
Combining the Right Tools and Talent To Manage Risk By Doug Stevens, Vice President of Managed Services at Aspire Technology Partners Security tools that protect the perimeter, endpoints and cloud are a critical part of your security architecture, but without the resources or wherewithal to monitor events on a consistent basis, your network is still […]

Wi-Fi 6 Has Changed the Way We Connect
BY Cody Harris, Director, Digital Architectures Nearly every device we use, whether it’s our cell phone, watch, tablet or computer connects using Wi-Fi. Historically, workspaces needed to be pre-wired to facilitate connections from user devices to the applications and data required to perform their job. This was done by running various cables through the walls […]
The Inherent Risks of the Roblox Game and Its Impact on Students
By Aspire Security Operations Center (SOC) Team Roblox is a free-to-play online game for Windows, Mac, iOS, Android, and Xbox. It is also a game creation platform that allows users to create their own games and play games created by other users. Roblox has a massive global player base. In 2021 alone, the game’s authors […]

Living in the Cloud and Modernizing Your Data Center – Part 1
Modernizing your data center — the right way — with a focus on the Cloud. By Christian Chavez, Data Center Cloud Solutions Architect The Cloud is a term often thrown around but rarely nailed down. But it’s essential to do so because of its ubiquity in today’s world. Businesses and consumers use the Cloud every […]

An Insider’s Guide to the New Webex App
Are you ready to make the move? By Stephen Howard, Solutions Engineer Cisco Webex has begun transitioning organizations from the older Webex Meetings App (Desktop App) to the Webex App. The Webex app is an all-inclusive collaboration platform with meetings, messaging, and calling rolled into a single application. Cisco started the migration process in January […]

