What is SASE, and why is it important?
By Manuel DeGuzman, Enterprise Network Solutions Architect
The Changing Network Landscape
The way we work has evolved, reshaping our networking and security landscapes. Mass adoption of Cloud applications and Software as a service (SaaS) in our everyday lives adds to the complexity of managing and securing our networks. Over a third of enterprise workloads are now on public clouds, and half reside in private clouds. It increases internet traffic, our dependency on higher speed, and reliable connectivity.
Add in the effects of the pandemic with remote work now being the standard for most organizations, and the result is a much different technology environment.
As more remote offices and branch locations pop up as businesses grow to expand reach, each branch location will typically require a WAN connection back to a hub location like the headquarters, a data center, or even to each other. These connections will need to be managed and secured. And the remote locations will typically require some level of technical support from headquarters.
Why SASE – Secure and optimized connections to the hub in a single platform
Originally, resources were primarily hosted in a local data center. Eighty percent of the bulk traffic was on the internal network where users accessed local information. Only 20% of the requests accessed the internet. The key was to have secure and optimized connections to the hub. Security was implemented at the branch offices and data center locations. Efforts to centralize security were lacking. Cloud-based resources were typically non-critical.
All that has changed; the internal vs. internet traffic ratio has flipped with 20% internal traffic and 80% traffic to the internet.
Some key trends have evolved over the past decade, reshaping the network and security landscape. What once was an on-prem-centric concept has morphed into adopting a SaaS model, with most workloads and applications now hosted in the cloud.
We need a solution that overcomes the challenge of inconsistent security, limited visibility and control, and varied end-user experience in a complex environment. Security needs to be robust and provide a consistent experience across users regardless of their location. Network and security teams need visibility of the entire network simultaneously, not in individual segments across multiple applications. SASE brings all this together on a single platform.
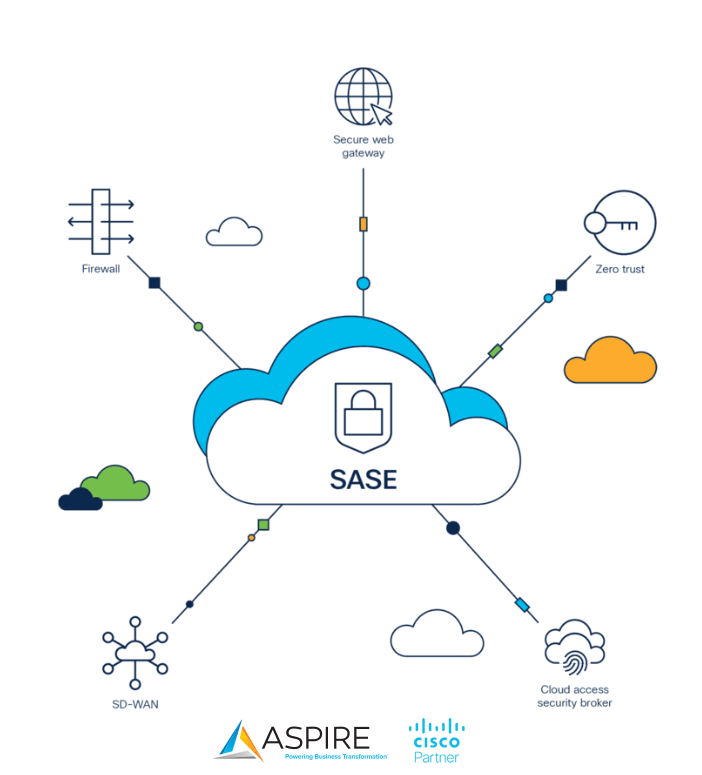
SASE – Secure Access Service Edge
SASE stands for Secure Access Service Edge. It is a consolidated architectural solution that provides effective and homogenous security and experience for users anywhere on any device.
SASE combines security and networking functionality into a single, fully integrated cloud-native platform.
It provides a consistent security and connection experience on any platform or location. You can be in the main office, a satellite office, a home office, or the coffee shop down the street. Your network and security staff have the same visibility into your network no matter where you access your work.
Building the Components for Your SASE Journey
- Software-defined wide-area networking (SD-WAN) – SD-WAN allows you to create a virtual wide area network that combines multiple transport services, including multiprotocol label switching (MPLS), cellular and 5G networks, Dedicated Internet Access (DIA) and broadband connections, to provide users in remote offices/locations access to corporate resources, applications, and services securely. SD-WAN enables increased visibility, control, performance, and optimization of WAN environments.
- Zero Trust – The concept is simple – never trust, always verify. Zero Trust verifies user identities and establishes device trust before granting access to your network and applications. Zero-trust means continuous monitoring and authentication of users and devices. A key component of this is Multifactor Identification (MFA). It relies on an independent device, such as a cell phone or mobile app to authenticate legitimate users. It may also be a code-generating device on your key ring, or a code sent as a text message. Financial and health organizations, such as banks or medical providers, have used this form of MFA for years. You need a combination of devices to access your network or account.
- Domain Name System (DNS) Security – DNS security is the first line of defense against threats and a terrific way to stop attacks before a user connects to a questionable website. Consider the DNS system as the internet’s phonebook as it holds the mapping of domain names to IP Addresses. DNS security uses a combination of databases of known bad actors and a series of other indicators to protect your network. It monitors DNS requests and blocks dangerous connections.
- Secure Web Gateway (SWG) is a cloud-based network security service that provides several security functions. It sits between an organization’s users and the internet. SWGs add malware detection, file sandboxing, and dynamic threat intelligence to your network. It can provide secure socket layer (SSL) decryption, application and content filtering, and data loss prevention (DLP) protections.
- Firewall as a service (FWaaS) delivers a cloud-based firewall solution to protect organizations. FWaaS typically includes Layer 3 and Layer 4 (IP, port, and protocol) visibility and control, along with Layer 7 (application control) rules and IP anonymization. FWaaS brings consistent policy enforcement for all users and locations with a single, centralized cloud-delivered firewall.
- Cloud access security broker (CASB) is on-premises or cloud-based security software that sits between cloud service users and cloud-service providers. It enforces an organization’s security policies and compliance requirements whenever cloud services or data is accessed. CASB can give insights into cloud application use and identify unauthorized use. Auto-discovery detects cloud applications in use and identifies high-risk applications, users, and other key risk factors. The capability to detect and provide alerts when abnormal user activity occurs helps stop internal and external threats to your data and business.
Threat Visibility/Observability provides an insight into service availability, application performance, end-to-end network metrics, end-user performance, and internet insights. It is essential to keep track of all your resources, how they perform and how they affect the user experience. This visibility gives you insight into performance issues for rapid remediation and consistent or improved user experience. Fully Integrated, Multifunctional, and Cloud-Delivered Platform
The networking and security landscape is evolving from discrete solutions to a fully integrated, multifunction, cloud-delivered networking and security platform. It is prevalent now because businesses increasingly need the flexibility to deploy services across their enterprise. There are more complex hurdles today than ever before. Companies need to control and secure internet access, manage on-prem and cloud applications and data, and provide protection for remote users all while reducing the strain on internal resources.
The need to manage remote offices and mobile/remote users is growing as we move from an in-person office model to work from anywhere. Remote users may be less inclined or not have the same level of access to help desk or security resources as in-person office staff.
Remote and work-from-home staff often do not think about the security of their internet connection. Cybercriminals see this as an opportunity to exploit vulnerabilities and send targeted attacks to unsuspecting users.
SaaS has become more prevalent in supporting critical business functions but has increased the attack plane. User authentication, robust and consistent security, and access control policies applied from a CASB solution can be pushed out to all users and endpoints from a single pane of glass.
Implementing SASE helps reduce the complexity for your staff. Rather than forcing your IT staff to learn multiple solutions and interfaces, SASE presents a cloud-based, single-pane-of-glass user experience. With lean IT staff being increasingly the norm, easy-to-use, effective solutions are critical. SASE is not an all-or-nothing proposition; it’s a journey. Each organization is different, moving on its path to implementation. Many companies deploy SASE in stages, initially focusing on security or WAN connectivity, then building from there.
Learn more about SASE and what it can do to protect your business. For inquiries and to talk to an Aspire expert, email us at Cybersecurity@aspiretransforms.com. Let Aspire Technology Partners guide you on the path toward your SASE implementation. Contact one of our specialists today.

Aspire Technology Partners is a Cisco Gold Integrator and Gold Provider engrained in solution pillars that set us apart as a true Cisco solutions provider. We are committed to the continuous improvement of expertise and skillsets around Cisco initiatives that enable us to help and guide customers in the adoption and management of technology architectures designed to transform their organization. We hold Cisco Master Specializations in Collaboration, Enterprise Networking, and Security and are one of only 25 partners in the US to receive the Cisco Advanced Customer Experience Specialization.