The Insider’s Guide to Cisco Software-Defined Access
What is Software-Defined Access?

Abstract/Introduction
As Software Defined Networks continue to disrupt the networking world, the need to fully understand how to design, operate, and optimize these networks becomes more and more important.
Problem Statement
Customer’s IT teams are strapped. Between lack of good resources in the candidate pool, and the need to stay up-to-date on the latest technologies becomes a daunting task. Software defined networks will alleviate this issue by making the administration of the network more intuitive and less cumbersome.
Background
Aspire, a Cisco Gold Certified Partner, has extensive expertise in the space and provides a good reference guide that discusses the benefits, including components and best practices when evaluating the solution.
Solution
The solution is the value that Aspire provides to the customer when trying to make this determination. Aspire leverages decades in the field, deploying SDN in real world environments that can help the customer make the best decision for their use case and budget.
Conclusion
Depending on the customer’s particular use case, upgrading to a software based network management methodology could provide a much better user experience for the customer’s employees, and Aspire can assist customers in making that decision.
References
Cisco Software-Defined Access: Introducing an Entirely New Era in Networking Solution Overview
Cisco Identity Services Engine Data Sheet
Cisco Identity Services Engine Ordering Guide
Cisco SD-Access Ordering Guide
Cisco introduced Software-Defined Access (SD-Access) last summer at Cisco Live. Built on the principles of Cisco Digital Network Architecture, Software-Defined Access is the industry’s first intent-based networking solution for the Enterprise. Cisco developed DNA to create a roadmap to digitization and a path to achieve immediate benefits of network automation, segmentation, assurance, and security. SD-Access augments DNA by providing intent-based policy, automation, and assurance for campus access networks.
Software-Defined technologies have become more widespread over the last three years. The term itself, like the technology associated with it, is new. Hardware once defined technologies. Each part of a network design was made up of physical hardware equipment and appliances. Software-defined technologies add a virtualization layer on top of the physical hardware underneath it to enable automation, programmability, speed, and agility.
SD-Access gives organizations a more streamlined way to build networks and to manage everything—from security to user access policies—inside the network. The solution provides policy-based automation across the network by using a single network fabric. The single network fabric provides complete network visibility; consistent management across the network; secure end-to-end segmentation for users and devices; automation of daily tasks to enforce network policies; adaptive learning based on business policies set up during the design stage of the workflow that will improve troubleshooting, proactive responses to breaches, and more.
More specifically, at the heart of SD-Access is the DNA Center Controller. The controller manages the network. Utilizing applications that live on the controller, you can design the network, set consistent policies and segmentation, secure it, create Virtual Networks and scalable group tags, and provision it via automation. The beauty of this is that it all happens from one single platform which you then continue to use for monitoring and assurance.
Cisco has invested heavily in software-defined solutions. Last summer, Cisco acquired Viptela to expand its SD-WAN portfolio. They offer different software-defined solutions for the data center, for the enterprise, for SD-WAN, and, now, for enterprise access.
SD-Access remains new and not yet widely adopted. It’s part of the new era of networking that aims to simplify and automate network management. Organizations have questions about the technology because it is new. I plan to answer a few questions I’ve heard from customers regarding SD-Access. Those questions include:
-
What are the benefits of SD-Access?
-
What platforms support SD-Access?
-
What hardware will organizations need?
-
Will organizations need to buy new equipment to support the technology?
-
What are the components of SD-Access?
-
What are the best practices for deploying and using SD-Access?
Benefits of Using SD-Access
The technology industry has shifted to developing solutions that have a more streamlined, simplified, security-focused, policy-first approach that is guided by contextual insights based on business intent. Ultimately, the major benefit of SD-Access is the business intent aspect. The business intent of your organization informs everything in your network and, in turn, helps you manage business outcomes.
Streamlined Design
With SD-Access, you can design your network, apply policies, provision network segmentation and user groups in a fraction of the time it would normally take to accomplish those tasks. This is all thanks to its streamlined intuitive workflow. It simplifies the building and management of your network. Each phase of the workflow has tools to define your network and your policies, to deploy your network, and to manage your network.
I’ll provide further definition around each phase of the workflow later in this blog.
Security and Segmentation
SD-Access separates user, lines of business, devices, and application traffic without redesigning the network via end-to-end segmentation. It helps secure your business against threats, as well as achieve compliance, and provide a foundation to enforce your network security policies.
Automating your security policies will allow your network to detect and intercept threats on all devices across your network in a proactive manner. As your network adapts to the policies you established, it will anticipate threats and alert you about a potential threat before an actor launches an attack on your network.
Policy Enforcement
You can set policies for both wired and wireless. You can apply the right policies for users, devices, and any application across the  network. It doesn’t matter where you log in, whether from home or the office, or from a hotel over a VPN connection. The device doesn’t matter either, because your automated policies will identify and tag the individual user on the network and then push out the correct policy based on user ID and tag.
network. It doesn’t matter where you log in, whether from home or the office, or from a hotel over a VPN connection. The device doesn’t matter either, because your automated policies will identify and tag the individual user on the network and then push out the correct policy based on user ID and tag.
Insights & Telemetry
SD-Access provides analytics and telemetry information to monitor and improve network health. The information they collect and provide significantly reduces troubleshooting time and helps executive leadership make informed decisions. All the information is aggregated into a single platform. You don’t need to look at various separated things anymore while troubleshooting an issue. Everything exists on one platform: the DNA Center.
Additionally, the rich insights into user behavior and application performance will help organizations improve employee productivity and the customer experience.
MAIN PARTS OF CISCO SD-ACCESS
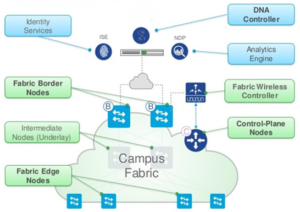
Software-Defined Access has four core components: 1) The DNA Center Controller; 2) the Network Fabric/Hardware 3) Cisco Identity Services Engine; and 4) DNA Advantage License. Each component works with the others to achieve network automation, assurance, and security. SD-Access isn’t what it is without each of the four components.
Those components are:
-
The DNA Center Controller
-
Cisco ISE 2.3 patch 1
-
Network Fabric
-
DNA Advantage Licensing on all hardware components
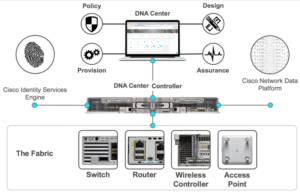
The DNA Center Controller provides the applications that you let you design, provision, automate, manage and monitor your SDA fabric. It also provides the integration, utilizing PXGrid, for Cisco ISE authentication and policy.
The network fabric supports the end-to-end segmentation, and programmability at a substantial scale to improve network performance. Network programmability is a key part of Cisco’s SDN vision.
Cisco ISE is a secure network access platform. ISE is an integral part of SD-Access for policy implementation, dynamic mapping of users to scalable group tags, and simplified security policy enforcement.
The DNA Advantage Licensing opens up the hardware to all of the required features required to interact with the DNA Controller to automate, provision, manage, and monitor the fabric.
The DNA Center Controller
DNA Center is an intuitive centralized management system that network engineers can use to design, provision, and apply policy across the SDA network. It centrally manages four workflow areas: design, policy, provision, and assurance.
DNA Center: Design, Policy, Provision, Assurance Definitions
Design should always come first in your workflow. You don’t need hardware components on-site on day zero to begin designing your network. You will have your controller on day zero. Once you rack it, power it on, assign an IP address, you can configure device global settings, network site profiles for physical device inventory, network hierarchy, network settings such as DHCP and DNS, ISE integration, and IP address management (IPAM) integration.
One point of confusion I’ve heard from customers during deployments is whether the controller becomes a DHCP or DNS server. It doesn’t. SD-Access is an intuitive intent-based network. This means it knows which devices and which servers play those roles based on the information you provide it during the provision stage of the workflow.
The policy should follow the design in your workflow. The policy stage allows you to define business intent for provisioning into the network, which includes the creation and management of virtual networks, assignment of endpoints to virtual networks, and policy contract definitions for groups, as well as scalable group tags for segmentation. The term ‘intent-based’ networking refers to policy. You’ll register your business intentions during this part of the workflow. Once you do that, your network will communicate them throughout the network.
Provision is the third stage of your workflow. At this point, you have designed your network, and you have created your policy. Now you’re ready to deploy it. You can provision devices for management and create fabric domains, your nodes (border; control plane; edge), and other SDA components such as fabric wireless.
A quick note about SD-Access Architecture: SDA Architecture includes an underlay network and overlay network. Both concern how your network communicates.
The underlay concerns communications between physical aspects of your network, such as the communications between the routers and switches. The DNA Center Controller lets you provision and automate your underlay. If you do provision the underlay with the controller, it means the controller will automatically select the IS-IS protocol. You can also choose to provision the underlay manually and you can utilize any dynamic routing protocol if you like. The underlay is completely Layer 3. No spanning-tree to worry about here.
The overlay allows your devices and endpoints to communicate with each other. The overlays are virtual networks that run over your physical underlay.
You’ll assign devices to different sites when you provision your fabric overlays. The takeaway is that you have complete control over provisioning, assignments, and roles for your network thanks to that aptly named DNA Center Controller.
Assurance is the final stage in your workflow. In a previous life, it had the name Network Data Platform (or NDP). Assurance is the analytics and telemetry engine and is responsible for your network’s health. Assurance provides 360-degree views for client-specific tasks (onboarding) and device-specific tasks (resource usage, loss and latency). You’ll have access to troubleshooting tools, as well as issue identification and resolution, and mean scores to let you know what the health of the network is.
Assurance reduces the time it takes to identify and resolve an issue. Formerly, an IT team needed to sort through logs and use different tools to identify the issue and then resolve it. This process could take a long time, significant resources, and cost. DNA Center and SD-Access completely automate the process of identification and resolution. Once Assurance detects an issue, you’ll receive a notification, followed by a proposed solution. You might follow the proposed solution, or you might not. If one or the other solution doesn’t properly resolve the issue, you can rewind, as it were, and return the network to a state with which you’re comfortable.
Single Network Fabric
The single network fabric enables a consistent user experience from anywhere without compromising network security. The single network fabric establishes network consistency. The policies you create with DNA Center and ISE create the consistent experience for your users, regardless if they’re connected wired or wirelessly, and regardless of where they connect from; whether it’s at home, in the office, on a VPN from a hotel, on your laptop, desktop, mobile device, or Chromebook.
ISE
DNA Center and ISE combine their forces to dynamically map users and devices to scalable group tags. Cisco created scalable group tags, also known as security group tags, because of shortcomings inherent in traditional approaches to policy administration.
Previously, network administrators established policies on a per-device basis. However, user growth and the proliferation of different device types has increased operational complexity and costs. The manual set-up of access points across a campus or a branch, along with the manual configuration of every access switch, required regular and time-consuming maintenance to keep pace with changes in technology. Users, devices, locations, time of access, and other valuable data points weren’t tracked or tagged when they connected to a network and accessed an application.
Scalable group tags resolved those shortcomings. With SGTs, all traffic is tagged based on the automatic profiling of the user by the access switch. The access switch determines the user’s ID, device, location, time of access, and other data points. The tag is a numerical value that the administrator manually assigns to access switches or that ISE automatically administers. ISE transmits the information to every supported device in the network so it knows what level of access to give the user.
ISE and the DNA Center Controller are tightly integrated. They communicate and speak the same language through authentication and certificate exchange. Once you integrate ISE with the controller, those components communicate, exchange certificates, and provision your user access policies.
SD-ACCESS NODES
Traditionally, network architects and engineers have used two-tiered, or three-tiered, networks where there’s a core, a distribution, and an access layer. And, in many ways, networking remains the same. Only the names of things have changed.
The SD-Access fabric is composed of four types of nodes: the border node; the edge node; the control plane node; and the intermediate nodes.
The border node and control plane nodes are the equivalents of the core; the intermediate nodes are the equivalent of the distribution layer; and the edge nodes are the equivalent to the access layer.
Fabric Border Node
The fabric border node communicates with traditional networks outside the fabric. It is the gateway. If you need to communicate with the Internet, you’ll use the fabric border node. At the time of this writing, you can deploy between 1-4 border nodes. I recommend always deploying the border nodes in pairs to eliminate single points of failure.
Border nodes are responsible for maintaining full internal route tables and full external route tables. Routing tables contain a set of rules that determine where network traffic is directed. Because of this responsibility, you need redundant, resilient, and capable hardware for your border node. I’ve listed the recommended hardware in the hardware section of the post.
Fabric Edge Node and Wireless Fabric Edge Node
Think of your fabric edge node as the access layer switch in a traditional campus design. Essentially, the edge node connects wired and devices to the SD-Access fabric.
Fabric Wireless Controller
The wireless controller is the sibling of the edge node. It connects wireless devices to the fabric.
Control Plane Node
Control plane nodes act as the network fabric’s traffic controllers and direct traffic between the edge nodes. It runs a host tracking database to map location information and Endpoint IDs to the location it needs. Once Border and Edge nodes send registration information to the control plane, the control plane node processes each resolution request to send Endpoint IDs to the requested/designated location.
The hardware you choose for your control plane nodes should be redundant, resilient, capable, and powerful. Why?
The control plane node has a /32 route for every single node on your network. So, if you have 10,000 endpoints on your network, you’ve got 10,000 /32s to keep track of. With that many endpoints on a control plane, you’ll want to make sure the control plane node is a powerful, redundant, resilient, and capable piece of hardware. For peace of mind, you’ll also want to deploy more than one. Two control plane nodes make life easier and boosts your redundancy. With the current release from Cisco, you can have up to two control plane nodes within your fabric.
Intermediate Nodes
Intermediate nodes don’t need to support SD-Access, which means you’re free to use non-Cisco devices. However, any device you do use needs to support Layer 3 and the routing protocol you selected for your underlay network. The intermediate nodes function as a distribution layer. These nodes only route IP traffic between the edge and border nodes.
In sum, the border nodes and control plane nodes are the equivalent of core switches; the intermediate nodes are the equivalent of distribution switches; the edge nodes are the equivalent of access layer switches.
SDA Hardware for Each Role
The hardware for your nodes is important in SD-Access. Using redundant, capable, fast, and powerful hardware is especially important. In this section, I listed the supported hardware for each type of node I wrote about in the above section.
Hardware for Border and Control Plane Nodes
- Cisco Catalyst 9500 Series Switches
- Cisco Catalyst 3850 Series Fiber Module
- Cisco Catalyst 6500 or 6807-XL Switch with Supervisor 2T
- Cisco Catalyst 6500 r 6807-XL Switch with Supervisor 6T
- Cisco Catalyst 6880-X Switch
- Cisco Catalyst 6840-X Switch
- Cisco Nexus 7700 Switch (Sup 2E, M3 line cards only)
- Cisco 4400 and 4300 Series Integrated Services Routers
- Cisco ASR 1000 Series Aggregation Services Routers
Hardware for Edge Nodes (like cloud switch layer)
- Cisco Catalyst 9300 Series Switches
- Cisco Catalyst 9400 Series Switches (Sup1)
- Cisco Catalyst 3850 Series and 3650 Series Switches
- Cisco Catalyst 4500E Series Switches (Sup8E, Sup9E)
SDA Hardware Compatibility
Organizations and companies do not have limitless budgets. Usually, organizations upgrade one part of its network once per year due to budget limitations. Organizations can’t buy new equipment and invest in new solutions every time the industry dictates it should.
It is fair to wonder whether technology you purchased not long ago within the last two years will be obsolete because of SD-Access. After all, if you’ve seen the marketing blitz for the Catalyst 9000 switches, you might think exactly that. Such a frenzied marketing blitz around not only the switches but around an entirely new era of networking suggests that Cisco is focused on the future and not so much on the older things from the past.
Cisco is well-aware of budget limitations. They’ve made older hardware (or hardware purchased within the last three years) compatible with the newer technologies and solutions they’ve developed and manufactured. While you’ll see the Catalyst 9000 switches associated with SD-Access and Cisco DNA, because they are the best and most optimal pieces of programmable hardware to use with SDA, the Catalyst 3850, 3650, and 4500 are compatible with SD-Access as well.
Other supported SDA hardware includes:
Cisco ISR & ASR routers
- From the ISR family:
- Cisco 4300s and 4400s
- From the ASR family:
- Cisco 1001-X and 1001-HX
- Cisco CSRv
- Nexus 7700
- with Sup 2-E and M3 Line cards Only
- Catalyst 6500 or 6807-XL
- With Sup2 T and Sup6T (code dependent)
- Catalyst 6840-X and 6880-X
- Catalyst 4500E Series
- With Sup 8E and 9E
Your wireless LAN controllers:
- Cisco 3504s
- Cisco 5520s
- Cisco 8540s
Your access point to Wave one and Wave two:
- Cisco 1700s
And now, Cisco Meraki also has integration with DNA Center Assurance.
SD-Access Best Practices and Conclusion
SD-Access is still new. Cisco announced it last summer. Organizations have deployed SD-Access slowly and selectively. They might deploy it on one floor of a new building or in a closet somewhere – or any isolated and controlled space.
 I’ve developed several best practices for phased deployments of the technology.
I’ve developed several best practices for phased deployments of the technology.
- Redundancy: Redundancy is important for SDA. Redundant power, chassis, and paths. Have A+B power. Have equal cross multi-pathing. Have redundant modules and chassis. In cases of downtime, redundancies will help you get back online, make changes, etc.
- Top Shelf Hardware for Nodes: Your control plane nodes (we recommend two), and your border nodes (we recommend 2-4) need top-shelf hardware with great power behind it (something like the Catalyst 9500 or ASR 1001-x).
- Have a Maximum Transmission Unit of 1542 across the board: A maximum transmission unit is the largest size packet or frame that can be sent in a packet or frame-based network. The standard is an MTU of 1500; however, the vxLAN that carries traffic from fabric edge to fabric edge adds an additional 42 bytes to the payload. You’ll suffer decreased performance, or a failed performance if the packet becomes larger than 1500 MTU.
Ultimately, we recommend an MTU of 9100 across all network underlay devices, which includes your:
- Fabric edge nodes
- Intermediate nodes
- Border nodes
- Control plane nodes
Making 9100 MTU the standard ensures your network won’t suffer decreased or failed performance.
- Follow the workflow: Following the workflow (design, policy, provision, assurance) will save you time and reduce the amount of time spent redoing work.
- Cluster DNA Center Controllers for Redundancy: You’ll lose visibility into your network if your network goes down if you use one controller. It would limit your ability, once back online, to make changes and adjust policies. If you choose to cluster, three DNA Center controllers or more are supported.
And there you have it: your complete insider’s guide into software-defined access. We have no doubts that this networking architecture is the wave of the future and will continue to make IT easier across the board for enterprises as they adopt it. Expect to see more about SD-Access as the need for automation and streamlined practices continues to grow. For more insights into Cisco architectures and technologies, feel free to check out our other resources and sign up for our Beyond The Data Sheet webinar series.


